In today’s rapidly evolving digital landscape, cloud computing has become the backbone of modern business operations. From small startups to multinational enterprises, the adoption of cloud services such as Google Workspace, Microsoft 365, Salesforce, AWS, and others has revolutionized the way organizations store, access, and manage data. However, this transformation comes with its fair share of challenges—particularly in the areas of security, compliance, and visibility. To address these challenges, many organizations are turning to a Cloud Access Security Broker—a powerful solution that helps monitor, secure, and control the use of cloud applications and data.
This is where Cloud Access Security Brokers (CASBs) come into play.
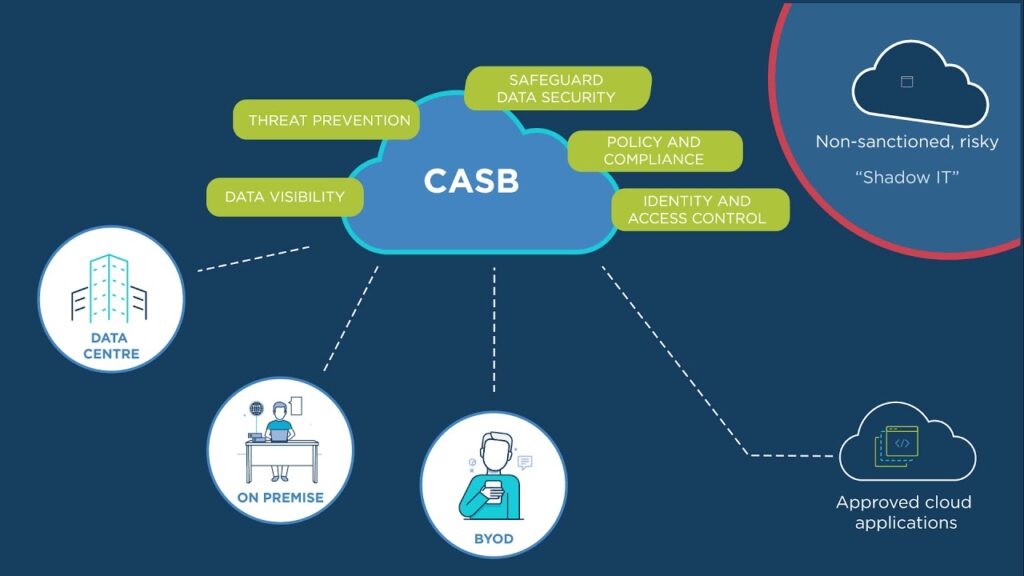
What Is a Cloud Access Security Broker (CASB)?
A Cloud Access Security Broker (CASB) is a security policy enforcement point positioned between cloud service users and cloud applications. CASBs act as intermediaries, providing visibility into cloud usage, enforcing security policies, ensuring compliance, and protecting sensitive enterprise data.
According to Gartner, a CASB is a software tool or service that sits between an organization’s on-premises infrastructure and a cloud provider’s infrastructure. Its main function is to monitor cloud activity and enforce security, compliance, and governance policies.
Key Functions of a Cloud Access Security Broker
A CASB typically provides four core functionalities:
- Visibility: Offers detailed insights into cloud application usage, including shadow IT.
- Compliance: Ensures data policies meet regulatory standards (e.g., GDPR, HIPAA).
- Data Security: Protects data through encryption, tokenization, and access controls.
- Threat Protection: Detects and mitigates threats like malware and unauthorized access.
Why Cloud Access Security Broker Is More Important Than Ever
With organizations moving critical operations and data to the cloud, they are also exposing themselves to new vulnerabilities. Traditional perimeter-based security tools are no longer sufficient in the cloud-native world. Consider these modern challenges:
- Shadow IT: Employees using unauthorized cloud apps.
- Data Leakage: Sensitive information being stored or shared in unprotected environments.
- Compliance Risks: Failure to meet industry-specific data regulations.
- Account Hijacking: Attackers gaining unauthorized access to cloud accounts.
- Insider Threats: Employees misusing cloud services either maliciously or accidentally.
This evolving threat landscape necessitates a cloud-native solution that provides end-to-end control and monitoring—hence the need for CASBs.
Types of Cloud Access Security Broker Deployments
There are three common CASB deployment models:
1. API-Based CASBs
- Connect directly to cloud service providers using APIs.
- Provide detailed activity logs, content inspection, and policy enforcement.
- Ideal for controlling data-at-rest and retroactive analysis.
2. Proxy-Based CASBs
- Intercept user traffic between the user and cloud services.
- Offer real-time monitoring and policy enforcement.
- Can be reverse proxy or forward proxy.
3. Hybrid CASBs
- Combine both API and proxy methods.
- Offer greater flexibility, comprehensive security, and policy coverage.
Core Capabilities of a CASB: Explained in Detail
1. Cloud Visibility
One of the key problems organizations face is shadow IT—unauthorized cloud services used by employees. A CASB can discover and monitor all cloud apps in use, even those outside the corporate-approved list. This helps organizations:
- Understand usage trends.
- Identify risky applications.
- Take action on unsanctioned apps.
A relevant example is how Netskope’s CASB enables real-time cloud visibility and risk scoring.
2. Data Security
CASBs provide a wide range of data protection mechanisms:
- Data Loss Prevention (DLP) to detect and prevent sensitive data from leaving the organization.
- Encryption and tokenization to protect data at rest and in transit.
- Access controls to limit who can access what and from where.
Explore how McAfee MVISION Cloud addresses data security in multi-cloud environments.
3. Compliance and Governance
A CASB helps enforce data policies aligned with:
By monitoring user behavior and data access, CASBs ensure that organizations remain compliant with industry regulations.
4. Threat Detection and Protection
Modern CASBs use machine learning and behavioral analytics to detect:
- Unusual user behavior
- Account takeovers
- Malware or ransomware uploads
- Insider threats
You can learn more about how Palo Alto Networks Prisma Cloud integrates threat intelligence into its CASB functionality.
Why Your Business Needs a CASB
Whether you are a startup or an established enterprise, if you use cloud services, you need a CASB. Here’s why:
1. Protects Sensitive Data in the Cloud
The biggest concern with cloud adoption is data security. CASBs secure sensitive data such as customer PII, financial records, and intellectual property stored in cloud services.
2. Provides Unified Security Across Multiple Clouds
Most organizations today use multiple SaaS, PaaS, and IaaS platforms. A CASB provides a centralized control layer to secure all cloud environments.
3. Ensures Regulatory Compliance
For industries such as healthcare, finance, and government, compliance is non-negotiable. CASBs automate compliance reporting and enforce standards across cloud platforms.
4. Monitors Shadow IT
Unmonitored cloud usage can lead to massive data breaches. CASBs provide visibility into all cloud activity, helping security teams take preventive action.
5. Enables Secure BYOD
With more employees using personal devices, securing endpoints accessing the cloud becomes essential. CASBs support context-aware access and multi-factor authentication for BYOD security.
Key CASB Use Cases Across Industries
Healthcare
- Enforce HIPAA compliance
- Secure electronic health records (EHR)
- Monitor third-party cloud applications
See how Symantec CloudSOC supports healthcare compliance.
Finance
- Protect financial data and transactions
- Comply with PCI-DSS and SOX
- Prevent insider trading and fraud
Education
- Manage student and faculty cloud access
- Protect academic records
- Ensure secure collaboration tools (Google Workspace, Microsoft 365)
Retail & E-commerce
- Protect customer PII and payment data
- Monitor employee access to cloud CRM tools
- Prevent data leakage to competitors
Leading Cloud Access Security Broker Providers in the Market
Choosing the right CASB vendor is critical. Here are some of the top providers:
1. Microsoft Defender for Cloud Apps
- Seamless integration with Microsoft 365 and Azure.
- Advanced analytics and threat protection.
2. Netskope CASB
- Highly scalable, hybrid deployment.
- Comprehensive DLP and threat protection.
- Supports over 30,000 cloud apps.
3. McAfee MVISION Cloud (Now Trellix)
- Strong DLP and policy enforcement.
- Works well with IaaS, PaaS, and SaaS.
4. Palo Alto Networks Prisma Cloud
- Offers full-stack security for apps, data, and infrastructure.
- Includes cloud workload protection and code-to-cloud coverage.
5. Cisco Cloudlock
- Agentless CASB.
- Integration with major SaaS apps.
- Focus on user behavior analytics.
How to Choose the Right Cloud Access Security Broker for Your Business
Selecting the right CASB depends on several factors:
- Cloud Usage
- Compliance Needs
- Deployment Preference
- Integration Capabilities
- Budget
You can compare leading CASBs using tools like G2’s CASB comparison page.
Challenges in CASB Implementation
- Complexity
- Latency
- Shadow IT Workarounds
- Cost
Organizations can minimize these challenges by working with experienced IT consultants and choosing CASBs with robust documentation and support.
Future Trends in CASB and Cloud Security
1. AI and Machine Learning
Read how AI is reshaping cloud security.
2. Zero Trust
CASBs are becoming integral to Zero Trust Architecture. Learn more from the NIST Zero Trust framework.
3. SASE Integration
Gartner predicts that SASE will play a major role in enterprise security.
FAQs: Cloud Access Security Brokers
Q1. Are CASBs only for large enterprises?
No. CASBs are scalable and benefit small, medium, and large organizations.
Q2. Do CASBs slow down network performance?
Proxy-based CASBs may introduce latency. API and hybrid models are more optimized.
Q3. Is a CASB the same as a firewall?
No. CASBs focus on cloud data protection, whereas firewalls protect network perimeters.
Q4. Can a CASB prevent insider threats?
Yes. CASBs use behavior analytics and DLP to detect and mitigate insider risks.
Q5. How long does deployment take?
Depending on complexity, it can range from days to weeks.
Conclusion
As businesses increasingly depend on cloud technologies, ensuring cloud security is no longer optional—it’s a necessity. A Cloud Access Security Broker (CASB) acts as a powerful ally in the fight against data breaches, compliance failures, and unauthorized cloud usage.
Whether your organization handles healthcare records, financial data, or customer information, a CASB provides a centralized, intelligent layer of security, visibility, and compliance. By investing in the right CASB solution, businesses can confidently embrace cloud innovation without compromising on security.



